Dark Web: Clever and Cute Security Innovations
December 11, 2024
 This write up was created by an actual 80-year-old dinobaby. If there is art, assume that smart software was involved. Just a tip.
This write up was created by an actual 80-year-old dinobaby. If there is art, assume that smart software was involved. Just a tip.
I am not sure how the essay / technical analysis “The Fascinating Security Model of Dark Web Marketplaces” will diffuse within the cyber security community. I want to highlight what strikes me as a useful analysis and provide a brief, high-level summary of the points which my team and I found interesting. We have not focused on the Dark Web since we published Dark Web Notebook, a complement to my law enforcement training sessions about the Dark Web in the period from 2013 to 2016.
This write up does a good job of explaining use of open source privacy tools like Pretty Good Privacy and its two-factor authentication. The write up walks through a “no JavaScript” approach to functions on the Dark Web site. The references to dynamic domain name operations is helpful as well.
The first observation I would offer is that in the case of the Dark Web site analyzed in the cited article is that the security mechanisms in use have matured and, in the opinion of my research team, advanced to thwart some of the techniques used to track and take down the type of sites hosted by Cyberbunker in Germany. This is — alas — inevitable, and it makes the job of investigators more difficult.
The second observation is that this particular site makes use of distributed services. With the advent of certain hosting providers to offer self managed virtual servers and a professed inability to know what’s happening on physical machines. Certain hosting providers “comply” and then say, “If you try to access the virtual machines, they can fail. Since we don’t manage them, you guys will have to figure out how to get them back up.” Cute and effective.
The third observation is that the hoops through which a potential drug customer has to get through are likely to make a person with an addled brain get clean and then come back and try again. On the other hand, the Captcha might baffle a sober user or investigator as well. Cute and annoying.
The essay is useful and worth reading because it underscores the value of fluid online infrastructures for bad actors.
Stephen E Arnold, December 11, 2024
Bitext NAMER: Simplifying Tracking of Translated Organizational Names
December 11, 2024
 This blog post is the work of an authentic dinobaby. No smart software was used.
This blog post is the work of an authentic dinobaby. No smart software was used.
We wrote a short item about tracking Chinese names translated to English, French, or Spanish with widely varying spellings. Now Bitext’s entity extraction system can perform the same disambiguation for companies and non-governmental entities. Analysts may be looking for a casino which operates with a Chinese name. That gambling facility creates marketing collateral or gets news coverage which uses a different name or a spelling which is different from the operation’s actual name. As a result, missing a news item related to that operation is an on-going problem for some professionals.
Bitext has revealed that its proprietary technology can perform the same tagging and extraction process for organizational names in more than two dozen languages. In “Bitext NAMER Cracks Named Entity Recognition,” the company reports:
… issues arise with organizational names, such as “Sun City” (a place and enterprise) or aliases like “Yati New City” for “Shwe Koko”; and, in general, with any language that is written in non-Roman alphabet and needs transliteration. In fact, these issues affect to all languages that do not use Roman alphabet including Hindi, Malayalam or Vietnamese, since transliteration is not a one-to-one function but a one-to-many and, as a result, it generates ambiguity the hinders the work of analysts. With real-time data streaming into government software, resolving ambiguities in entity identification is crucial, particularly for investigations into activities like money laundering.
Unlike some other approaches — for instance, smart large language models — the Bitext NAMER technology:
- Identifies correctly generic names
- Performs type assignment; specifically, person, place, time, and organization
- Tags AKA (also known as) and pseudonyms
- Distinguishes simile names linked to unelated entitles; for example, Levo Chan.
The company says:
Our unique method enables accurate, multilingual entity detection and normalization for a variety of applications.
Bitext’s technology is used by three of the top five US companies listed on NASDAQ. The firm’s headquarters are in Madrid, Spain. For more information, contact the company via its Web site, www.bitext.com.
Stephen E Arnold, December 11, 2024
FOGINT: Pavel Durov: A Waffling Borzoi with a Shock Collar Now?
December 11, 2024
 Information from the FOGINT research team. No smart software involved.
Information from the FOGINT research team. No smart software involved.
Cointelegraph, one of the “future of money” news services covering crypto ran an interesting story on Saturday, December 7,2024. “Telegram Found Pavel Durov Questioned in Paris Court for First Time: Report.” We know this is a blog post about a write up sharing information from another source. Keep this dicey chain in mind.
The core of the story is that Pavel Durov was under the control of French authorities in August 2024. Wikipedia reports that Mr. Durov may have met with Vladimir Putin before jetting to Paris and landing at Paris-Le Bourget Airport. In the last three months, information about Mr. Durov’s and his lawyer’s interaction with the French authorities has been limited. After 90 days of having his movements restricted, Mr. Durov has been rumored to:
- Expressed a desire to cooperate with law enforcement when duly authorized requests for alleged bad actors is provided to “Telegram”, which is Mr. Durov for practical purposes. Pavel’s brother Nikolai seems pre-occupied with technical issues related to the Telegram platform.
- Telegram has apparently agreed to interact with organizations focused on preventing human trafficking and child sexual abuse material
- Reversing course on his statements about responding to government pressure. One example was Telegram’s blocking of Ukrainian content from Ukrainian government agencies to Telegram users in Russia and possibly other countries in the Russian Federation.
Here’s what Cointelegraph reported:
Durov appeared in a Parisian court at 10 am CET on Dec. 6, alongside his lawyers David-Olivier Kaminski and Christophe Ingrain.
The lawyers have offices at 126 Boulevard St. Germain. Kaminski’s Web site says:
We specialize in criminal defense. The Kaminski law firm has built up recognized expertise in all areas of criminal defense. We can represent our clients at any stages of the judicial procedure, including police custody, preliminary investigation, judicial information, criminal court and before the assize court). The firm defends individuals as well as companies, legal entities, or institutions (Non-governmental organizations, associations, professional bodies). Kaminski’s catchphrase is, “The culture and practice of criminal defense is respect for fundamental freedoms.” https://www.kaminskiavocats.com/
Christophe Ingrain is part of the defense team. He was / is affiliated with Darrois Villey Maillot Brochier. He was named one of the 30 most influential lawyers in France, and he appeared on a list of the “best layers” in France. His office is on Avenue Victor Hugo.
According to Cointelegraph:
An anonymous source familiar with the matter told the Agence France-Presse (AFP) that the questioning focused on the allegations tied to Telegram’s potential use for illicit transactions. When asked about the legal proceedings, Durov reportedly told the AFP that he “trusts the French justice” system but refused to elaborate on the case.
His “refusal” to comment means that the 40 year old with more than 100 children is listening to his French attorneys. He may also have been informed about France’s low profile prison system. La Santé was built in 1867 and entertains a number of high-risk criminals. For those who chat with French law enforcement officials, La Santé is often described as a place one goes but never leaves. This prison has a VIP section which is somewhat different from the VIP services available for online gamblers in pursuit of an ejunket. It is located in the 14th arrondissement. There are two other facilities in Paris as well. France also has some special purpose prisons located near military bases and allegedly a couple of in-ground facilities in North Africa. If “in-ground” does not resonate with you, you may not want to know the set at these alleged incarceration facilities. As a point of reference, French prisons are overcrowded but c’est dommage. As a rule of thumb one may want to avoid getting ensnared in the French judiciary or prison system. Red tape is a specialty of French bureaucrats, and it can be a challenging situation for defendants and their lawyers.
Cointelegram observes:
Industry insiders are worried that the case against Durov raises alarming concerns for privacy-preserving Web3 technologies.
The Web3 reference includes blockchain technology, distributed infrastructures like Telegram’s, distributed finance, and a number of other innovations. These can add to the investigative burden of law enforcement and tax authorities.
Durov has paid bail of $5 to $6 million. However, Cointelegraph points out:
If convicted, Durov could face up to 10 years in prison and a fine of €500,000 ($550,000).
Was Durov’s interaction with French authorities an accident or coincidence? No. France allegedly began a preliminary investigation if February 2024. In July 2024 that was promoted to a judicial inquiry. In August, he was apprehended.
Sean Brizendine, a blockchain researcher, told Beyond Search:
Mr. Durov definitely appears to be listening to his high-power legal team. He is obviously aware that everything is at stake.
Net net: FOGINT wonders if the prosecution of CSAM perpetrators will ramp up as Durov demonstrates his willingness to cooperate. What’s at risk for Telegram is that the significant push into crypto services could be derailed. Other “free speech” advocates will create alternative services, but that will be expensive and time consuming. The core of Telegram is not available as open source software. Most cyber professionals are not aware of the scope of the Telegram platform.
Stephen E Arnold, December 11, 2024
KPMG FOMO on AI
December 11, 2024
 This blog post flowed from the sluggish and infertile mind of a real live dinobaby. If there is art, smart software of some type was probably involved.
This blog post flowed from the sluggish and infertile mind of a real live dinobaby. If there is art, smart software of some type was probably involved.
AI is in demand and KPMG long ago received the message that it needs to update its services to include AI consulting services in its offerings. Technology Magazine shares the story in: “Growing KPMG-Google Cloud Ties Signal AI Services Shift.” Google Cloud and KPMG have a partnership that started when the latter’s clients wanted to implement Google Cloud into their systems. KPMG’s client base increased tenfold when they deployed Google Cloud services.
The nature of the partnership will change to Google’s AI-related services and KPMG budgeted $100 million to the project. The investment is projected to give KPMG $1 billion in revenue for its generative AI technology. KPMG deployed Google’s enterprise search technology Vertex AI Search into its cloud services. Vertex AI and retrieval augmented generation (RAG), a process that checks AI responses with verified data, are being designed to analyze and assist with market and research analysis.
The partnership between these tech companies indicates this is where the tech industry is going:
“The partnership indicates how professional services firms are evolving their technology practices. KPMG’s approach combines its industry expertise with Google Cloud’s technical infrastructure, creating services that bridge the gap between advanced technology and practical business applications… The collaboration also reflects how enterprise AI adoption is maturing. Rather than implementing generic AI solutions, firms are now seeking industry-specific applications that integrate with existing systems and workflows. This approach requires deep understanding of both technical capabilities and sector-specific challenges.”
Need an accounting firm? Well, AI is accounting. Need a consultant. Well, AI is consulting. Need motivated people to bill your firm by the hour at exorbitant fees? You know whom to call.
Whitney Grace, December 11, 2024
The EU Cafeteria Wants to Serve Grilled Google
December 10, 2024
 This write up was created by an actual 80-year-old dinobaby. If there is art, assume that smart software was involved. Just a tip.
This write up was created by an actual 80-year-old dinobaby. If there is art, assume that smart software was involved. Just a tip.
How does one cook a kraken (a Norwegian octopus)? Here’s the recipe from Garlic & Zest:
- Clean the octopus, remove the beak(s) and place them in a large, heavy pot or Dutch oven.
- Add the vegetables, wine and corks.
- Bring to a boil, reduce heat to a simmer and cook for 45 minutes to one hour.
The hapless octopus awaits its fate. The goal is to serve up tasty individual dishes and follow up with a refreshing takoyaki. Thanks, MidJourney. Looks tasty.
I want to point out that the creature dies in this process. Now to the write up:
“Google Split Still on the Table, New EU Antitrust Chief Says” reports:
A potential split of Google’s business is still under consideration, according to Teresa Ribera, the European Union’s new competition chief, who also pledged to build bridges with incoming US President Donald Trump.
That’s the intent to grill the delectable sea monster, according to some children’s books.
The person setting the menu and supervising the chefs who will chop off the tentacles, remove its beak (ouch!), tenderize the helpless creature, and plop it on the barbie is Teresa Ribera.
For those who don’t follow Spain’s emergent leaders, Ms. Ribera is a socialist who will find some philosophical points of difference between her new kitchen team and the Wild West chuckwagon approach taken toward Google in the US of A.
The cited news story says the new EU Antitrust chef (sorry, I meant chief) allegedly said:
“It’s [chopping up Google] something that is of course on the table, and we try to work together with other relevant competition authorities worldwide, including the US competition authorities,” she said. ‘It is important to take into consideration this potential division, divestment of some of these businesses. We will be assessing case-by-case.”
The question is, “When will the main course be served?” Restaurant kitchens — like Brussels, the French and German governments — can be chaotic places.
Stephen E Arnold, December 10, 2024
Amazon Offers to Fight Crime, Not on Its Platform But in the District of Columbia No Less
December 10, 2024
 This blog is created by a dinobaby and his helpers who are neither AI nor dinobabies. If there is fancy art, please, assume that smart software contributed. Dinobabies can barely think let alone draw.
This blog is created by a dinobaby and his helpers who are neither AI nor dinobabies. If there is fancy art, please, assume that smart software contributed. Dinobabies can barely think let alone draw.
Amazon has been busy explaining how its smart software will make Alexa Live Again! Meanwhile some legal eagles have been dropping documents on the digital bookstore and its happy, happy employees and contractors. This news reached me via the for-sale outfit CNBC, a talking heads program on “real” TV. “Amazon Sued by DC Attorney General for Allegedly Excluding Neighborhoods from Prime Delivery” reports what may be obvious to anyone who has worked in the District of Columbia or gone for a late night walk alone on a hot summer evening in some interesting parts of the District. Oh, the slogan for the DC entity is “Taxation without Representation.”
Senior professionals for a high-technology company reach consensus. The giant firm will help law enforcement address certain issues. Thanks, MidJourney. Good enough.
The CNBC story says:
Washington, D.C.’s attorney general sued Amazon on Wednesday [yep, CNBC, that was December 4, 2024], accusing the company of covertly depriving residents in certain ZIP codes in the nation’s capital from access to Prime’s high-speed delivery. The lawsuit from AG Brian Schwalb alleges that, since 2022, Amazon has “secretly excluded” two “historically underserved” D.C. ZIP codes from its expedited delivery service while charging Prime members living there the full subscription price. Amazon’s Prime membership program costs $139 a year and includes perks like two-day shipping and access to streaming content.
The idea is that a DC resident pays $139 a year to get “Prime” treatment only to get the shaft; that is, no delivery for you, pilgrim.
Amazon took time out from its Alexa Lives Again! activities to issue a statement. According to the “real” news source a really happy Amazon professional allegedly said:
Amazon spokesperson Kelly Nantel said in a statement it’s “categorically false” that its business practices are “discriminatory or deceptive.” “We want to be able to deliver as fast as we possibly can to every zip code across the country, however, at the same time we must put the safety of delivery drivers first,” Nantel said in a statement. “In the zip codes in question, there have been specific and targeted acts against drivers delivering Amazon packages. We made the deliberate choice to adjust our operations, including delivery routes and times, for the sole reason of protecting the safety of drivers.” Nantel said Amazon has offered to work with the AG’s office on efforts “to reduce crime and improve safety in these areas.”
I like the idea of a high technology outfit trying to reduce crime. I have been the victim of Amazon fraud. I like to mention the women’s underwear shipped to me instead of the $600 Ryzen CPU I ordered. A more recent example was Amazon’s emailing me a picture of a stranger’s door with the message, “Your package has been delivered.” I spent about an hour trying to get a human to address the issue. The response, I think, was we will credit you for the order. When? How? Sorry, I have no idea because the happy Amazon professional based in a third party customer service facility had no clue. I am thinking, “Why doesn’t Amazon do something about the fraud on its own platform?”
I personally have zero confidence that Amazon can address such issues in the District of Columbia. It is known to one resident — my son, who lives in the District — has observed porch pirates following Amazon delivery vans. As soon as the package is left, the porch pirate exits the chase vehicle and takes the package. The fix ranges from designated pick up points in certain vulnerable areas of the District to having a security team follow the porch pirates on their rental scooters, Teslas, and other vehicles. Of course, the alternative is to go to a store like REI in the District of Columbia, shop, and return home. (Oh, sorry, I forgot that Amazon’s business practices have contributed to the demise of brick and mortar retail. Oh, well. It was just a dinobaby thought.)
This will be an interesting legal case to follow. Porch pirates follow Amazon delivery vehicles and prove the value of paying attention.
Stephen E Arnold, December 10, 2024
We Need a Meeting about Meetings after I Get Back from a Meeting
December 10, 2024
 This blog post flowed from the sluggish and infertile mind of a real live dinobaby. If there is art, smart software of some type was probably involved.
This blog post flowed from the sluggish and infertile mind of a real live dinobaby. If there is art, smart software of some type was probably involved.
I heard that Mr. Jeff Bezos, the Big Daddy of online bookstores, likes chaotic and messy meetings. Socrates might not have been down with that approach.
As you know, Socrates was a teacher who ended up dead because he asked annoying questions. “Socratic thinking” helps people remain open to new ideas. Do new ideas emerge from business meetings? Most of those whom I know grumble, pointing out to me that meetings waste their time. Michael Poczwardowski challenges that assumption with Socratic thinking in the Perspectiveship post “Socratic Questioning – ‘Meetings are a waste of time’”.
Socratic-based discussions are led by someone who only asks questions. By asking only questions the discussion can then focus on challenging assumptions, critical thinking, and first principles-dividing problems into basic elements to broaden perspectives and understanding. Poczwardowski brings the idea that: “meetings are a waste of time” to the discussion forum.
Poczwardowski introduces readers to Socratic thinking with the steps of classification, challenge assumptions, look for data/evidence, change perspective, explore consequences and implications, and question the question. Here’s my summary done my a person with an advanced degree in information science. (I know I am not as smart as Google’s AI, but I do what I can with my limited resources, thank you.)
“The key is to remain open to possibilities and be ready to face our beliefs. Socratic questioning is a great way to work on improving our critical thinking.
When following Socratic questioning ask to:
• Clarify the idea: It helps us understand what we are talking about and to be on the same page
• Challenge assumptions: Ask them to list their assumptions.
• Look for evidence: Asking what kind of evidence they have can help them verify the sources of their beliefs
• Change perspectives: Look at the problem from others’ points of view.
• Explore consequences: Explore the possible outcomes and effects of actions to understand their impact”
Am I the only one who thinks this also sounds obvious? Ancient philosophers did inspire the modern approach to scientific thought. Galileo demonstrated that he would recant instead of going to prison or being killed. Perhaps I should convene a meeting to decide if the meeting is a waste of time. I will get back to you. I have a meeting coming up.
Whitney Grace, December 10, 2024
AI Automation: Spreading Like Covid and Masks Will Not Help
December 10, 2024
 This blog post flowed from the sluggish and infertile mind of a real live dinobaby. If there is art, smart software of some type was probably involved.
This blog post flowed from the sluggish and infertile mind of a real live dinobaby. If there is art, smart software of some type was probably involved.
Reddit is the one of the last places on the Internet where you can find quality and useful information. Reddit serves as the Internet’s hub for news, tech support, trolls, and real-life perspectives about jobs. Here’s a Reddit downer in the ChatGPT thread for anyone who works in a field that can be automated: “Well this is it boys. I was just informed from my boss and HR that my entire profession is being automated away.”
For brevity’s sake here is the post:
“For context I work production in local news. Recently there’s been developments in AI driven systems that can do 100% of the production side of things which is, direct, audio operate, and graphic operate -all of those jobs are all now gone in one swoop. This has apparently been developed by the company Q ai. For the last decade I’ve worked in local news and have garnered skills I thought I would be able to take with me until my retirement, now at almost 30 years old, all of those job opportunities for me are gone in an instant. The only person that’s keeping their job is my manager, who will overlook the system and do maintenance if needed. That’s 20 jobs lost and 0 gained for our station. We were informed we are going to be the first station to implement this under our company. This means that as of now our entire production staff in our news station is being let go. Once the system is implemented and running smoothly then this system is going to be implemented nationwide (effectively eliminating tens of thousands of jobs.) There are going to be 0 new jobs built off of this AI platform. There are people I work with in their 50’s, single, no college education, no family, and no other place to land a job once this kicks in. I have no idea what’s going to happen to them. This is it guys. This is what our future with AI looks like. This isn’t creating any new jobs this is knocking out entire industry level jobs without replacing them.”
The post is followed by comments of commiseration, encouragement, and the usual doom and gloom. It’s not surprising that local news stations are automating their tasks, especially with the overhead associates with employees. These include: healthcare, retirement package, vacation days, PTO, and more. AI is the perfect employee, because it doesn’t complain or take time off. AI, however, is lacking basic common sense and fact checking. We’re witnessing a change in how the job market, it just sucks to live through it.
Whitney Grace, December 10, 2024
Amazon: Black FridAI for Smart Software Arrives
December 9, 2024
 This write up was created by an actual 80-year-old dinobaby. If there is art, assume that smart software was involved. Just a tip.
This write up was created by an actual 80-year-old dinobaby. If there is art, assume that smart software was involved. Just a tip.
Five years ago, give or take a year, my team and I were giving talks about Amazon. Our topics touched on Amazon’s blockchain patents, particularly some interesting cross blockchain filings, and Amazon’s idea for “off the shelf” smart software. At the time, we compared the blockchain patents to examining where data resided across different public ledgers. We also showed pictures of Lego blocks. The idea was that a customer of Amazon Web Service could select a data package, a model, and some other Amazon technologies and create amazing AWS-infused online confections.
Thanks, MidJourney. Good enough.
Well, as it turned out the ideas were interesting, but Amazon just did not have the crate engine stuffed in its digital flea market to make the ideas go fast. The fix has been Amazon’s injections of cash and leadership attention into Anthropic and a sweeping concept of partnering with other AI outfits. (Hopefully one of these ideas will make Amazon’s Alexa into more than a kitchen timer. Well, we’ll see.)
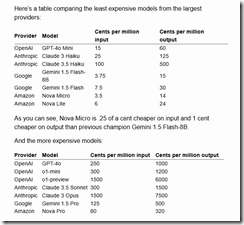
I read “First Impressions of the New Amazon Nova LLMs (Via a New LLM-Bedrock Plugin).” I am going to skip the Amazon jargon and focus on one key point in the rah rah write up:
This is a nicely presented pricing table. You can work through the numbers and figure out how much Amazon will “save” some AI-crazed customer. I want to point out that Amazon is bringing price cutting to the world of smart software. Every day will be a Black FridAI for smart software.
That’s right. Amazon is cutting prices for AI, and that is going to set the stage for a type of competitive joust most of the existing AI players were not expecting to confront. Sure, there are “free” open source models, but you have to run them somewhere. Amazon wants to be that “where”.
If Amazon pulls off this price cutting tactic, some customers will give the system a test drive. Amazon offers a wide range of ways to put one’s toes in the smart software swimming pool. There are training classes; there will be presentations at assorted Amazon events; and there will be a slick way to make Amazon’s smart software marketing make money. Not too many outfits can boost advertising prices and Prime membership fees as part of the smart software campaign.
If one looks at Amazon’s game plan over the last quarter century, the consequences are easy to spot: No real competition for digital books or for semi affluent demographics desire to have Amazon trucks arrive multiple times a day. There is essentially no quality or honesty controls on some of the “partners” in the Amazon ecosystem. And, I personally received a pair of large red women’s underpants instead of an AMD Ryzen CPU. I never got the CPU, but Amazon did not allow me to return the unused thong. Charming.
Now it is possible that this cluster of retail tactics will be coming to smart software. Am I correct, or am I just reading into the play book which has made Amazon a fave among so many vendors of so many darned products?
Worth watching because price matters.
Stephen E Arnold, December 9, 2024
Hiding Messages: The You-Will-Not-Pay-Attention Tactic
December 9, 2024
 This blog post flowed from the sluggish and infertile mind of a real live dinobaby. If there is art, smart software of some type was probably involved.
This blog post flowed from the sluggish and infertile mind of a real live dinobaby. If there is art, smart software of some type was probably involved.
I worked on a project in Bogota, Columbia. One of the individuals with whom I interacted talked about steganography. This is a method for placing “content” inside of images. At the time which was probably a decade ago, the law enforcement officials in Columbia had encountered certain bad actors passing messages using steganography within images of a day at the beach with kids, beach balls, and happy gringos.
“Square Zero: Hide Silly Messages in Decorative Borders” explains how an innocuous graphic element in an image or any content object can convey information about a drug deal, a weapons pick up point, or a money laundering contact location. The write up says:
So how successful was the card [containing the swizzled border]? Well, we sent out about 40 of them; almost no one realized there was a puzzle on the card. Once nudged, most folks realized it was the border, and quite a few guessed binary was involved. At this point I’d suggest decoding it. The most common reply? “I think I’ll go on living my life, but thanks”
That’s the purpose of steganography: Making the message invisible or “secret.” Steganography, according to the online ad vendor Google, is “the practice of concealing information within another message or physical object to avoid detection.” The example described in the cited blog post works.
If you want to fiddle around with the technology, the cited article contains code and some technical explanation. I want to call your attention to what might be accomplished in an activity involving big money and real life-and-death circumstances. Consider this border which I downloaded from Free Clipart:
Let’s assume that a bad actor has encoded a message in this clip art.
To make the challenge more interesting, the bad actor has included additional information is an image embedded in the manipulated clip art frame:
How can this double up message embedding be accomplished? The answer is, “Use the sample code provided and some odds and ends from GitHub, and you are good to go.”
Does this application of “borders” and embedded images pose challenges to analysts, investigators, and law enforcement professionals? Some information, as I have stated before, should not be out and about, providing bad actors with ideas and enablers.
Stephen E Arnold, December 9, 2024