Microsoft: A Faint Signal from Employees or Just Noise from Gousers?
June 29, 2023
![Vea4_thumb_thumb_thumb_thumb_thumb_t[1] Vea4_thumb_thumb_thumb_thumb_thumb_t[1]](http://arnoldit.com/wordpress/wp-content/uploads/2023/06/Vea4_thumb_thumb_thumb_thumb_thumb_t1_thumb-35.gif) Note: This essay is the work of a real and still-alive dinobaby. No smart software involved, just a dumb humanoid.
Note: This essay is the work of a real and still-alive dinobaby. No smart software involved, just a dumb humanoid.
I spotted this story in my newsfeed this morning: “Leaked Internal Microsoft Poll Shows Fewer Employees Have Confident in Leadership and Gave the Worst Score to a Question about Whether Working There Is a Good Deal.”
My yellow lights began to flash. I have no way of knowing if the data were compiled in a rigorous, Statistics 101 manner. I have no way of determining if the data were just made up the way a certain big wheel at Stanford University handled “real” data. I have no way of knowing if the write up and the facts were a hallucination generated by a “good enough” Microsoft Edge smart output.
Nevertheless, I found the write up amusing.
Consider this passage:
The question about confidence in leaders got an average of 73% favorable responses across the company in this year’s poll compared to 78% in last year’s, according to results viewed by Insider.
I think that means the game play, the Solarwinds’ continuing siroc, and the craziness of moments (if this does not resonate, don’t ask).
Let’s assume that the data are faked or misstated. The question which arises is here in Harrod’s Creek, Kentucky, is: Why now?
Stephen E Arnold, June 29, 2023
Microsoft Code: Works Great. Just Like Bing AI
June 9, 2023
![Vea4_thumb_thumb_thumb_thumb_thumb_t[1] Vea4_thumb_thumb_thumb_thumb_thumb_t[1]](http://arnoldit.com/wordpress/wp-content/uploads/2023/06/Vea4_thumb_thumb_thumb_thumb_thumb_t1_thumb-8.gif) Note: This essay is the work of a real and still-alive dinobaby. No smart software involved, just a dumb humanoid.
Note: This essay is the work of a real and still-alive dinobaby. No smart software involved, just a dumb humanoid.
For Windows users struggling with certain apps, help is not on the way anytime soon. In fact, reports TechRadar, “Windows 11 Is So Broken that Even Microsoft Can’t Fix It.” The issues started popping up for some users of Windows 11 and Windows 10 in January and seem to coincide with damaged registry keys. For now the company’s advice sounds deceptively simple: ditch its buggy software. Not a great look. Writer Matt Hanson tells us:
“On Microsoft’s ‘Health’ webpage regarding the issue, Microsoft notes that the ‘Windows search, and Universal Windows Platform (UWP) apps might not work as expected or might have issues opening,’ and in a recent update it has provided a workaround for the problem. Not only is the lack of a definitive fix disappointing, but the workaround isn’t great, with Microsoft stating that to ‘mitigate this issue, you can uninstall apps which integrate with Windows, Microsoft Office, Microsoft Outlook or Outlook Calendar.’ Essentially, it seems like Microsoft is admitting that it’s as baffled as us by the problem, and that the only way to avoid the issue is to start uninstalling apps. That’s pretty poor, especially as Microsoft doesn’t list the apps that are causing the issue, just that they integrate with ‘Windows, Microsoft Office, Microsoft Outlook or Outlook Calendar,’ which doesn’t narrow it down at all. It’s also not a great solution for people who depend on any of the apps causing the issue, as uninstalling them may not be a viable option.”
The write-up notes Microsoft says it is still working on these issues. Will it release a fix before most users have installed competing programs or, perhaps, even a different OS? Or maybe Windows 11 snafus are just what is needed to distract people from certain issues related to the security of Microsoft’s enterprise software. Will these code faults surface (no pun intended) in Microsoft’s smart software. Of course not. Marketing makes software better.
Cynthia Murrell, June 9, 2023
Microsoft Bing Causes the Google Lights to Flicker
May 10, 2023
 Note: This essay is the work of a real and still-alive dinobaby. No smart software involved, just a dumb humanoid.
Note: This essay is the work of a real and still-alive dinobaby. No smart software involved, just a dumb humanoid.
The article “The Updated Bing Chat Leapfrogs ChatGPT in 6 Important New Ways” shakes the synapses of Googzilla. The Sundar & Prabhakar Comedy Show has been updating its scripts and practicing fancy dancing. Now the Redmond software, security, and strategy outfit has dragged fingernails across the chalk board in Google World. Annoying? Yes, indeed.
The write up does not mention Google directly, but the eerie light from the L.E.D.s illuminating the online ad vendor’s logo shine between the words in the article. Here’s an example:
opening up access to all.
None of this “to be” stuff from the GOOG. The Microsofties are making their version of ChatGPT available to “all.” (Obviously the categorical “all” is crazy marketing logic, but the main idea is “here and now”, not a progressive or future tense fantasy land.
Also, the write up uses jargon to explain what’s new from the skilled professionals who crafted Windows 3.11. Microsoft has focused on the image generation feature and hooking more people who want smart software into the Edge world of a browser.
But between the spaces in the article, one message flickers. Microsoft is pushing product. Google is reorganizing, watching Dr. Jeff Dean with side glances, and running queries to find out what Dr. Hinton is saying about the online ad outfit’s sense of ethical behavior. In short, the Google is passive with synapses jarred by Microsoft marketing plus actual applications of smart software.
Fascinating. Is the flickering of the Google L.E.D.s a sign that power is failing or flawed electrical engineering is causing wobbles?
Stephen E Arnold, May 10, 2023
Google Panic: Just Three Reasons?
April 20, 2023
 Note: This essay is the work of a real and still-alive dinobaby. No smart software involved, just a dumb humanoid.
Note: This essay is the work of a real and still-alive dinobaby. No smart software involved, just a dumb humanoid.
I read tweets, heard from colleagues, and received articles emailed to me about Googlers’ Bard disgruntlement? In my opinion, Laptop Magazine’s summary captures the gist of the alleged wizard annoyance. “Bard: 3 Reasons Why the Google Staff Hates the New ChatGPT Rival.”
I want to sidestep the word “hate”. With 100,000 or so employees a hefty chunk of those living in Google Land will love Bard. Other Google staff won’t care because optimizing a cache function for servers in Brazil is a world apart. The result is a squeaky cart with more squeaky wheels than a steam engine built in 1840.
The three trigger points are, according to the write up:
- Google Bard outputs that are incorrect. The example provided is that Bard explains how to crash a plane when the Bard user wants to land the aircraft safely. So stupid.
- Google (not any employees mind you) is “indifferent to ethical concerns.” The example given references Dr. Timnit Gebru, my favorite Xoogler. I want to point out that Dr. Jeff Dean does not have her on this weekend’s dinner party guest list. So unethical.
- Bard is flawed because Google wizards had to work fast. This is the outcome of the sort of bad judgment which has been the hallmark of Google management for some time. Imagine. Work. Fast. Google. So haste makes waste.
I want to point out that there is one big factor influencing Googzilla’s mindless stumbling and snorting. The headline of the Laptop Magazine article presents the primum mobile. Note the buzzword/sign “ChatGPT.”
Google is used to being — well, Googzilla — and now an outfit which uses some Google goodness is in the headline. Furthermore, the headline calls attention to Google falling behind ChatGPT.
Googzilla is used to winning (whether in patent litigation or in front of incredibly brilliant Congressional questioners). Now even Laptop Magazine explains that Google is not getting the blue ribbon in this particular, over-hyped but widely followed race.
That’s the Code Red. That is why the Paris presentation was a hoot. That is why the Sundar and Prabhakar Comedy Tour generates chuckles when jokes include “will,” “working on,” “coming soon” as part of the routine.
Once again, I am posting this from the 2023 National Cyber Crime Conference. Not one of the examples we present are from Google, its systems, or its assorted innovation / acquisition units.
Googzilla for some is not in the race. And if the company is in the ChatGPT race, Googzilla has yet to cross the finish line.
That’s the Code Red. No PR, no Microsoft marketing tsunami, and no love for what may be a creature caught in a heavy winter storm. Cold, dark, and sluggish.
Stephen E Arnold, April 26, 2023
Google versus Microsoft: Whose Marketing Is Wonkier?
April 17, 2023
 Note: This essay is the work of a real and still-alive dinobaby. No smart software involved, just a dumb humanoid.
Note: This essay is the work of a real and still-alive dinobaby. No smart software involved, just a dumb humanoid.
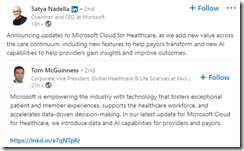
I want to do what used to be called a comparison. I read Microsoft’s posts on April 12, 2023 (I don’t know for certain because LinkedIn does not provide explicit data and time information because who really cares about indexing anymore.) The first post shown in the screenshot is from the Big Dog himself at Microsoftland. The information is one more announcement about the company’s use of OpenAI’s technology in another Microsoftland product. I want to shout, “Enough already,” but my opinion is not in sync with Microsoft’s full-scale assault on Microsoft users. It is now a combination of effective hyperbole and services designed to “add value.” The post below Mr. Nadella’s is from another Softie. The main point is that Microsoft is doing smart things for providers and payors. My view is that Microsoft is doing this AI thing for money, but again my view is orthogonal to the company which cannot make some of its software print on office printers.
Source: LinkedIn 2023 at shorturl.at/egnpz. Note: The LinkedIn url is a long worm thing. I do not know if the short url will render. If not, give Microsoft’s search function a whirl.
Key takeaways: Microsoft owns a communications channel. Microsoft posts razzmatazz verbiage about smart software. Microsoft controls the message. Want more? Just click the big plus and Microsoft will direct more information directly at you, maybe on your Windows 11 start menu.
Now navigate to “Sundar Pichai’s Response to the Delayed Launch of Bard Is Brilliant and Reminds Us Why Google Is Still Great.” I want to cry for joy because the Google has not lost the marketing battle with Microsoft. I want to shout, “Google is number one.” I want to wave Googley color pom poms and jump up and down. Join me. “Google is number one.”
The write up strikes me as a remarkable example of lip flapping and arm waving; to wit:
Google secures its competitive advantage not necessarily by being the fastest to act, but by staying the course on why it exists and what it stands for. Innovation and product disruption is baked into its existence. From its operating models to its people strategy, everything gets painted with a stroke of ingenuity, curiosity, and creativity. While other companies may have been first to market with new technologies or products, Google’s focus on innovation and improving upon existing solutions has allowed it to surpass competitors and become the market leader in many areas.
The statements in this snippet are remarkable for several reasons:
- Google itself announced Code Red, a crisis. Google itself called Mom and Dad (Messrs. Brin and Page) to return to the Mountain View mothership to help figure out what to do after Microsoft’s Davos AI blizzard. Google itself has asked every employee to work on smart software. Now Google is being cautious. Is that why Googler Jeff Dean has invested in a ChatGPT competitor?
- Google is killing off products. The online magazine with the weird logo published “The Google Graveyard” in 2019. On April 12, 2023, Google killed off something called Currents. Believe it or not, the product was to replaced Google Plus. Yeah, Google really put wood behind the hit for a social media home run.
- The phrase “ingenuity, curiosity, and creativity” does not strike me as the way to sum up how Google operates. I think in terms of “poaching and paying for the GoTo, Overture, Yahoo online advertising inspiration,” perfecting the swinging door so all parties to an ad deal pay Google, and speaking like a wandering holy figure when answering questions before a legal body.
Key takeaways: Google relies on a PR firm or a Ford F 150 Lightning carrying Google mouse pads to get a magazine to write an article which appears to be a reality not reflected by the quite specific statements and actions of the Google.
Bottom-line: Microsoft bought a channel. Google did not. Google may want to consider implementing the “me too” approach and buy an Inc.-type publication. I am now going to be increasingly skeptical of the information presented by Inc. Magazine. I already know to be deeply suspicious of LinkedIn.
Stephen E Arnold, April 17, 2023
Gotcha, Googzilla: Bing Channels GoTo, Overture, and Yahoo with Smart Software
April 5, 2023
 Note: This essay is the work of a real and still-alive dinobaby. No smart software involved, just a dumb humanoid.
Note: This essay is the work of a real and still-alive dinobaby. No smart software involved, just a dumb humanoid.
I read “That Was Fast! Microsoft Slips Ads into AI-Powered Bing Chat.” Not exactly a surprise? No, nope. Microsoft now understands that offering those who want to put a message in front of eye balls generates money. Google is the poster child of Madison Avenue on steroids.
The write up says:
We are also exploring additional capabilities for publishers including our more than 7,500 Microsoft Start partner brands. We recently met with some of our partners to begin exploring ideas and to get feedback on how we can continue to distribute content in a way that is meaningful in traffic and revenue for our partners.
Just 7,500? Why not more? Do you think Microsoft will follow the Google playbook, just enhanced with the catnip of smart software? If you respond, “yes,” you are on the monetization supersonic jet. Buckle up.
Here are my predictions based on what little I know about Google’s “legacy”:
- Money talks; therefore, the ad filtering system will be compromised by those with access to getting ads into the “system”. (Do you believe that software and human filtering systems are perfect? I have a bridge to sell you.)
- The content will be warped by ads. This is the gravity principle: Get to close to big money and the good intentions get sucked into the advertisers’ universe. Maybe it is roses and Pepsi Cola in the black hole, but I know it will not contain good intentions with mustard.
- The notion of a balanced output, objectivity, or content selected by a smart algorithm will be fiddled. How do I know? I would point to the importance of payoffs in 1950s rock and roll radio and the advertising business. How about a week on a yacht? Okay, I will send details. No strings, of course.
- And guard rails? Yep, keep content that makes advertisers — particularly big advertisers — happy. Block or suppress content that makes advertisers — particularly big advertisers – unhappy.
Do I have other predictions? Oh, yes. Why not formulate your own ideas after reading “BingBang: AAD Misconfiguration Led to Bing.com Results Manipulation and Account Takeover.” Bingo!
Net net: Microsoft has an opportunity to become the new Google. What could go wrong?
Stephen E Arnold, April 5, 2023
Laws, Rules, Regulations for Semantic AI (No, I Do Not Know What Semantic AI Means)
March 31, 2023
 Note: This essay is the work of a real and still-alive dinobaby. No smart software involved, just a dumb humanoid.
Note: This essay is the work of a real and still-alive dinobaby. No smart software involved, just a dumb humanoid.
I am not going to dispute the wisdom and insight in the Microsoft essay “Consider the Future of This Decidedly Semantic AI.” The author is Xoogler Sam Schillace, CVP or corporate vice president and now a bigly wizard at the world’s pre-eminent secure software firm. However, I am not sure to what the “this” refers. Let’s assume that it is the Bing thing and not the Google thing although some plumbing may be influenced by Googzilla’s open source contributions to “this.” How would you like to disambiguate that statement, Mr. Bing?
The essay sets forth some guidelines or bright, white lines in the lingo of the New Age search and retrieval fun house. The “Laws” number nine. I want to note some interesting word choice. The reason for my focus on these terms is that taken as a group, more is revealed than I first thought.
Here are the terms I circled in True Blue (a Microsoft color selected for the blue screen of death):
- Intent. Rule 1 and 3. The user’s intent at first glance. However, what if the intent is the hard wiring of a certain direction in the work flow of the smart software. Intent in separate parts of a model can and will have a significant impact on how the model arrives at certain decisions. Isn’t that a thumb on the scale?
- Leverage. Rule 2. Okay, some type of Archimedes’ truism about moving the world I think. Upon rereading the sentence in which the word is used, I think it means that old-school baloney like precision and recall are not going to move anything. The “this” world has no use for delivering on point information using outmoded methods like string matching or Boolean statements. Plus, the old-school methods are too expensive, slow, and dorky.
- Right. Rule 3. Don’t you love it when an expert explains that a “right” way to solve a problem exists. Why then did I have to suffer through calculus classes in which expressions had to be solved different ways to get the “right” answer. Yeah, who is in charge here? Isn’t it wonderful to be a sophomore in high school again?
- Brittle. Rule 4. Yep, peanut brittle or an old-school light bulb. Easily broken, cut fingers, and maybe blinded? Avoid brittleness by “not hard coding anything.” Is that why Microsoft software is so darned stable? How about those email vulnerabilities in the new smart Outlook?
- Lack. Rule 5. Am I correct in interpreting the use of the word “lack” as a blanket statement that the “this” is just not very good. I do love the reference to GIGO; that is, garbage in, garbage out. What if that garbage is generated by Bard, the digital phantasm of ethical behavior?
- Uncertainty. Rule 6. Hello, welcome to the wonderful world of statistical Fancy Dancing. Is that “answer” right? Sure, if it matches the “intent” of the developer and the smart software helping that individual. I love it when smart software is recursive and learns from errors, at least known errors.
- Protocol. Rule 7. A protocol is, according to the smart search system You.com is:
In computer networking, a protocol refers to a set of rules and guidelines that define a standard way of communicating data over a network. It specifies the format and sequence of messages that are exchanged between the different devices on the network, as well as the actions that are taken when errors occur or when certain events happen.
Yep, more rules and a standard, something universal. I think I get what Microsoft’s agenda has as a starred item: The operating system for smart software in business, the government, and education.
- Hard. Rule 8. Yes, Microsoft is doing intense, difficult work. The task is to live up to the marketing unleashed at the World Economic Forum. Whew. Time for a break.
- Pareidolia. Rule 9. The word means something along the lines is that some people see things that aren’t there. Hello, Bruce Lemoine, please. Oh, he’s on a date with a smart avatar. Okay, please, tell him I called. Also, some people may see in the actions of their French bulldog, a certain human quality.
If we step back and view these words in the context of the Microsoft view of semantic AI, can we see an unintentional glimpse into the inner workings of the company’s smart software? I think so. Do you see a shadowy figure eager to dominate while saying, “Ah, shucks, we’re working hard at an uncertain task. Our intent is to leverage what we can to make money.” I do.
Stephen E Arnold, March 31, 2023
Ethical AI: Let Us Not Take Our Eye Off the Money Ball, Shall We?
March 15, 2023
What full-time job includes an automatic ejection seat?
Flying an F 35? Yes.
Working on ethical and responsible smart software? Yes. A super duper ejection module too.
I wonder if Google’s enabling of the stochastic parrot conference and the Dr. Timnit Gebru incident made an impression on Microsoft? Hmmm. I the information in “Microsoft Just Laid Off One of Its Responsible AI Teams” is accurate, Microsoft’s management has either [a] internalized the Google approach or [b] missed the memorandum describing downstream effects of deprecating “responsible AI.”
The image above was output by craiyon.com. True, one of the Beyond Search researchers added the evil red eye and the pile of cash. We think the evil eye and the money illustrate where ethical behavior ranks among the priorities of some senior executives.
The write up by two of the Land of Bank Crashes favorites reports:
Microsoft laid off its entire ethics and society team within the artificial intelligence organization as part of recent layoffs that affected 10,000 employees across the company … The move leaves Microsoft without a dedicated team to ensure its AI principles are closely tied to product design …
The article is about 1,500 words, and I suggest you work through the essay/news/chest thumper.
Several observations:
- The objective is control, not ethical control. Just control.
- Smart software knows how to string together words, not what the words connote.
- MBAs with incentive plans view ethics as an interesting concept but one with the appeal of calculating their bonuses on an Amiga computer.
Net net: What exactly is the news about a big tech company trimming its ethics professionals? I thought it was standard operating procedure.
PS. I admire the begging for sign up pleas as well. Classy for some “real news” write ups. Ejection seat activated.
Stephen E Arnold, March 15, 2023
Bing Begins, Dear Sundar and Prabhakar
March 9, 2023
Note: Note written by an artificial intelligence wonder system. The essay is the work of a certified dinobaby, a near80-year-old fossil. The Purple Prose parts are made up comments by me, the dinobaby, to help improve the meaning behind the words.
I think the World War 2 Dear John letter has been updated. Today’s version begins:
Dear Sundar and Prabhakar…
“The New Bing and Edge – Progress from Our First Month” by Yusuf Mehdi explains that Bing has fallen in love with marketing. The old “we are so like one another, Sundar and Prabhakar” is now
“The magnetic Ms. OpenAI introduced me to her young son, ChatGPT. I am now going steady with that large language model. What a block of data! And I hope, Sundar and Prabhakar, we can still be friends. We can still chat, maybe at the high school reunion? Everyone will be there. Everyone. Timnit Gebru, Jerome Pesenti, Yan Lecun, Emily Bender, and you two, of course.”
The write up does not explicitly say these words. Here’s the actual verbiage from the marketing outfit also engaged in unpatchable security issues:
It’s hard to believe it’s been just over a month since we released the new AI-powered Bing and Edge to the world as your copilot for the web. In that time, we have heard your feedback, learned a lot, and shipped a number of improvements. We are delighted by the virtuous cycle of feedback and iteration that is driving strong Bing improvements and usage.
A couple of questions? Is the word virtuous related to the word virgin? Pure, chaste, unsullied, and not corrupted by … advertising? Has it been a mere 30 days since Sundar and Prabhakar entered the world of Code Red? Were they surprised that their Paris comedy act drove attendees to Le Bar Bing? Is the copilot for the Web ready to strafe the digital world with Bing blasts?
Let’s look at what the love letter reports:
- A million new users. What’s the Google pulled in with their change in the curse word policy for YouTube?
- More searches on Le Bing than before the tryst with ChatGPT. Will Google address relevance ranking of bogus ads for a Thai restaurant favored by a certain humanoid influencer?
- A mobile app. Sundar and Prabhakar, what’s happening with your mobile push? Hasn’t revenue from the Play store declined in the last year? Declined? Yep. As in down, down, down.
Is Bing a wonder working relevance engine? No way.
Is Bing going to dominate my world of search of retrieval? For the answer, just call 1 800 YOU WISH, please.
Is Bing winning the marketing battle for smarter search? Oh, yeah.
Well, Sundar and Prabhakar, don’t let that Code Red flashing light disturb your sleep. Love and kisses, Yusuf Mehdi. PS: The high school reunion is coming up. Maybe we can ChatGPT?
Stephen E Arnold, March 9, 2023
Unpatchable Windows Flaw? Will Surprises Reside in Smart Software from Microsoft?
March 7, 2023
No big deal? A flaw described as “Unpatchable”? Not to worry. Okay, I will pretend not to worry, but I am worrying. Many commercial and government systems may be at risk. “Stealthy UEFI Malware Bypassing Secure Boot Enabled by Unpatchable Windows Flaw” reports:
Researchers on Wednesday [presumably March 1, 2023] announced a major cybersecurity find—the world’s first-known instance of real-world malware that can hijack a computer’s boot process even when Secure Boot and other advanced protections are enabled and running on fully updated versions of Windows.
Microsoft’s good enough engineering has produced technology which in “unpatchable.” Shouldn’t that effort be directed toward creating software which is patchable? I know. I know. People are in a hurry. There are those TikToks to watch. Plus, who wants to fool around with secure boot issues when the future is smart software.
As the Microsofties chase after the elusive “it understands human utterance” bunny rabbit, what gotchas will be tucked inside ChatGPT-inspired applications? I am not very good at predicting the future. I am not dumb enough to say, “Hey, that Microsoft smart software will be okay.” Microsoft is good at marketing. May I suggest that Microsoft is not so good at producing software that meets users’ expectations for security.
Stephen E Arnold, March 7, 2023