US Government Censorship: Remarkable Assertion
September 28, 2022
I am not familiar with the censorship action described in “The U.S. Government’s Vast New Privatized Censorship Regime.”
One passage struck me as interesting; to wit:
At least 11 federal agencies, and around 80 government officials, have been explicitly directing social media companies to take down posts and remove certain accounts that violate the government’s own preferences and guidelines for coverage on topics ranging from COVID restrictions, to the 2020 election, to the Hunter Biden laptop scandal.
One of the characteristics of any government, including the US government, is that coordination across, among, and between agencies and individuals is time consuming, difficult, and fraught with missteps. I have no doubt that any broad US government activity is difficult to set up, implement, and keep outside the ken of Washington Post-type investigative journalists. Furthermore, getting one — let alone a group — of Silicon Valley type high tech outfits to take prompt action runs counter to my experience. If a government professional wants to obtain information believed to be available to a high tech outfit, the process often begins with a form. If the government professional, a specific point of contact will be known to the official. A phone call, email, or text message may or may not elicit a response. I have heard such statements as “Wow, blue bubble green bubble problem”, “I must have missed that email; I will look in my spam folder”, and “Can you send a hard copy request via FedEx?’ have been offered as reasons for typically slow responses to queries.
I know that information and outputs during the time of Covid was a bit of a challenge. I am not sure that anyone knew much about what others were doing. I will grant that the signals cited in the write up paint a picture of focused US government action concerning the conference and statement involved. But, if true, the actions are not what I would call “routine” behavior. Toss in third parties and the write up’s description of purposeful action is even more anomalous. Maybe I worked in less organized government entities.
I wish I had a nickel every time a project on which I have worked was described differently from what was actually going on.
Nevertheless, the write up is interesting.
Stephen E Arnold, September 28, 2022
Amazon Needs More Lobbyists, More Former Government Professionals… Pronto!
September 26, 2022
I have no idea about Amazon’s lobbying efforts. I don’t want to know. The money spent on DC insiders and Beltway Bandits makes me wish I still lived in the DC area. Selling work? Not too tough for those with connections. Heh, heh, if you know what I mean. Also, I am not confident that the modern RNA treatment for Potomac Fever works. What is supposed to chug along with reasonable predictability is influence peddling.
“Amazon Loses Effort to Exclude Jassy and Bezos from Testifying in FTC Prime Probe” seems to highlight an instance when events don’t go according to a plan. I learned from the allegedly real news CNBC story:
The Federal Trade Commission late Wednesday rejected Amazon’s bid to exclude CEO Andy Jassy and founder Jeff Bezos from testifying in a probe into the retail giant’s Prime program.
I can hear the “Commissioner, thank you for that question. I don’t know the complete answer. I will have the information you request sent to your office, etc, etc.”
Prime is a subscription or membership or a knock off of a low rent country club. Members get special treatment; for example, Thursday night football games, allegedly better-faster-cheaper delivery, and benefits at an Amazon grocery store like free delivery. Sorry, strike that free delivery for any Prime member. There’s even a page which explains what a member-subscriber-spender gets at this link and here.
The write up says:
The FTC has been investigating sign-up and cancellation processes for Amazon’s Prime program since March 2021. The agency is looking into whether Amazon deceives users into signing up for Prime, while failing to provide a simple way to cancel and avoid recurring charges. The Prime subscription program, which costs $139 a year and includes perks like free shipping, now has some 200 million subscribers worldwide. Amazon said last month it has been complying with the FTC’s requests so far, producing some 37,000 pages of documents.
I am curious about other Amazon business activities which may warrant some scrutiny; for example, certain interesting content on Twitch, products which appear to be from a well known “brand” but are slightly different from those in old fashioned stores, and the mechanisms for charging for certain functions on AWS.
Amazon Fire up the C-SPAN, get the popcorn, and tally the number of “thank you for the question” answers. Exciting. A bit late in the Monopoly game, but good theater.
Lobbyists will be watching to learn what to put in their next pitch to the Amazonians assigned to make this hearing stuff go away.
Stephen E Arnold, September 26, 2022
The UK and EU Demonstrate an Inability to Be Googley
September 15, 2022
In the grand scheme of operating a revolving door, the Google is probably going to adjudicate and apologize / explain. I call this “explagize,” an art form perfected at the GOOG. But what’s a revolving door? Visualize a busy pre-Covid building in midtown Manhattan. To enter, one pushes a panel of glass and the force spins a wagon wheel of similar doors. Now imagine that one pays every time one goes around. That’s how the Google online ad business works? Banner adds, pay. Pay to play, pay. Pay for AdWords, caching. Want analytics about those ads? Pay. The conceptual revolving door, however, does not allow the humanoid to escape either without fear of missing out on a sale or allowing a competitor to get clicks and leads and sales.
The BBC article “Google Faces €25bn Legal Action in UK and the EU” states:
The European Commission and its UK equivalent are investigating whether Google’s dominance in the ad tech business gives it an unfair advantage over rivals and advertisers.
This is old news, right? What’s different is this statement:
Damien Geradin, of the Belgian law firm Geradin Partners – which is involved in the Dutch case – said, “Publishers, including local and national news media, who play a vital role in our society, have long been harmed by Google’s anti-competitive conduct. “It is time that Google owns up to its responsibilities and pays back the damages it has caused to this important industry. “That is why today we are announcing these actions across two jurisdictions to obtain compensation for EU and UK publishers.”
Do you think “pay back” means a painful procedure capped with a big number fine? I do.
What’s not being considered, in my opinion, are these factors:
- The barristers, avocets, and legal eagles trying to wrest big bucks from Googzilla are unlikely to find the alleged monopolist eager to retain their firms’ services or look favorably on hiring the progeny of these high fliers
- Will the UK and EU spark counter measures; for example, prices may rise and some ad services not offered to outfits in the UK and EU?
- Will the UK and EU grasp the fact that ad options may not be able to fill any gap or service pull out from the Google?
- The high value data which Google allegedly has and under some circumstances makes available to government authorities may go missing because Google either suffered a machine failure or curtailed investment in infrastructure so that the data are disappeared.
More than money? Yep. Consequences after decades of hand waving and chicken salad fines may cause some governments to realize that their power, influence, and degrees of freedom are constrained by a certain firm’s walled garden.
The money for the fine? Too little and too late as I try to make sense of the situation. The spinning revolving door can be difficult to escape and trying may cause dizziness, injury, or company death. Yikes.
Stephen E Arnold, September 15, 2022
IBM Power10 Rah Rah: One Concerning Statement
September 12, 2022
IBM is back in the marketing game. Everyone wants a Power10 computer in a mobile phone or a MacBook Air form factor. Am I right! Yes.
The article “IBM Power10 Shreds Ice Lake Xeons for Transaction Processing.” This is a big iron made less big. The article points out use cases for those AIX users. Plus there are references to notable big iron outfits like Oakridge and Lawrence Livermore Labs, both really common computing environments like those in the local Coca-Cola distributor’s office or the regional garbage outfit’s offices in three cities.
The charts are phenomenal. Here’s an example. Look at how the blue bar is lower than the gray bar. And the power savings and the thermal data? You know what air conditioners are for as well as those nifty Caterpillar generators in the parking lot are for, don’t you?
Very encouraging.
But…
I noticed one sentence which gave me pause; to wit:
IBM will, of course, make some competitive wins, mostly in emerging markets (and in some cases as Inspur sells iron in China), and it will also win some deals for new kinds of workloads like MongoDB, EnterpriseDB, or Redis.
With the export restrictions imposed by the US on China, will the Power10 find its way to the Middle Kingdom? The use cases for Power10 at US national laboratories may exist in a country wrestling with some real estate issues. Can the Power10 help with the land and construction challenges? What about Chinese academics-only, please research outfits?
In the midst of a PR type content marketing article, I found the reference to China interesting. Will anyone else?
Stephen E Arnold, September 12, 2022
Google News Provides Access to Bombshell about Google
September 9, 2022
I thought that the Google had a news deal of some type with the GOOG and its news service. If you are not familiar with Google News (the ad free thing for many years) is available at this link. Google News included a story called “Google Pays ‘Enormous’ Sums to Maintain Search-Engine Dominance, DOJ Says.” Now this is not news here in Harrod’s Creek. Isn’t a modest payment provided to the people’s friend Apple to provide search results? Maybe? Maybe not?
What I find interesting is that locating the story on Google News required using the string “Google Search Engine Dominance.” [Note: This may require a payment to read unless one views the story via Google News. Maybe Google and Bloomberg have a special operation underway? Gee, I don’t know.] Other queries were less helpful. Interesting? Nah. Just the black box of Google News search working its magic. (Maybe that’s why Google Dorks are so darned popular among certain analysts and research-minded individuals. The information is in Google, but it can require a few cartwheels to locate in my experience.)
What was the main point of this Bloomberg story. (When I think of Bloomberg, I do associate the company with the chips on motherboards which phone home. Was this story accurate, true, grounded in verifiable data, or a confection like some social media mavens output? Again I don’t know. As I get older, I realize I don’t know much, if anything.)
The Bloomberg Google story on Google News says:
Alphabet Inc.’s Google pays billions of dollars each year to Apple Inc., Samsung Electronics Co. and other telecom giants to illegally maintain its spot as the No. 1 search engine, the US Justice Department told a federal judge Thursday [September 8, 2022].
News flash. This is not news. What is mildly interesting is that the US government after decades of finding joy in Google mouse pads, T shirts, and other tchotchkes is sort of investigating. (Why was it so darned difficult to get French income tax forms to come up in Google search results? Were those cranky folks at Foundem blowing smoke? You know the answer: I don’t know.
The write up continues:
“Google invests billions in defaults, knowing people won’t change them,” Dintzer told Judge Amit Mehta during a hearing in Washington that marked the first major face-off in the case and drew top DOJ antitrust officials and Nebraska’s attorney general among the spectators. “They are buying default exclusivity because defaults matter a lot.” Google’s contracts form the basis of the DOJ’s landmark antitrust lawsuit, which alleges the company has sought to maintain its online search monopoly in violation of antitrust laws.
Okay, written contracts. That’s something sort of concrete I suppose.
In my opinion, the best line in the Google story on Google News from good and friendly Bloomberg is this one:
“Default exclusivity allows Google to systemically deny rivals’ data,” he said.
If true, does this mean that former Googler Eric Schmidt was off base when he said that fear of Qwant was keeping him awake at night?
Probably not. But Google seems to have been taking steps to reduce the probability of Qwant or any other search engine gaining traction somewhat seriously. Does Google know its search system is only useful when one masters the machinations of the Dorkers?
Again: I don’t know.
Stephen E Arnold, September 9, 2022
Tweet Terror in Some Geographic Areas
September 8, 2022
While western countries are chided for controversial engagement with LGBTQ groups, they cannot compare the staunch hatred they face in the Middle East. The Middle East is dominated by fundamentalist Islamic governments that criminalize homosexuality and transgender people. Unfortunately, these groups experienced a new wave of hatred Euro News reported in, “Arabic Anti-LGBTQ Campaign Goes On Twitter.”
The anti-LGBTQ campaign is called Fetrah, meaning “human instinct” in Arabic. Three Egyptian marketing professionals experienced in social media campaigns designed Fetrah. Fetrah promotes only two genders, rejects homosexuality, and supporters show a blue and pink flag.
Meta deleted the Fetrah page, but supporters managed to get a different page up on Facebook as well as on Instagram. Unlike other social media platforms, Twitter does not ban hate groups like Fetrah:
“Mahsa Alimardani, a digital rights expert told the Cube that Twitter and other social media platforms should be investing more resources into fighting this harmful campaign. ‘Too much censorship and policing can actually be a problem on some platforms but with Twitter we often find that the reverse is true, especially when it comes to harassment and harmful content targeting vulnerable communities’ said Alimardini. ‘We can see here a prime example of how queer communities in the Middle Eastern and North African regions can be harmed by Twitter’s inaction. The platform has very high threshold when it comes to policing content, which can be harmful,’ she added.”
Western countries have their faults, but many people have a “live and let live” attitude when it comes to LGBTQ people. People in the Middle East are not that different, but hatred is unfortunately promoted by religious governments.
Whitney Grace, September 8, 2022
US Federally Funded Research: Open Access, Folks
September 7, 2022
In a surprise announcement, reports Ars Technica, “US Government to Make All Research it Funds Open Access on Publication.” The new policy was issued by the Office of Science and Technology Policy (OSTP) at the end of August. We expect this will be a windfall for researchers—in and outside the US. Though the US government is believed to be the world’s largest funder of scientific research, only those paying for subscriptions to academic journals have had access to many (most?) publicly funded studies. Writer John Timmer notes this constraint has loosened in recent years as a result of increased open-access journals and, especially with COVID-19 research, a trend toward preprints. We learn:
“Some people involved in scientific publishing worried that these trends would undercut the finances of the entire publishing industry, while others hoped to push them to open up all scientific publishing. This tension played out in the halls of Congress, where competing legislation would mandate or block open access to federal research. A truce of sorts was reached during the Obama administration. For federally funded research, publishers had two choices: either make the publication open access from the start or have subscription-only access for a year before opening things up. Government-sponsored repositories were opened to host copies of papers that weren’t made open access on the publisher’s site. In the intervening time, there has been a lot of growth in open access journals, and many subscription journals allowed authors to pay a fee to immediately open published papers. Most subscription journals also offered COVID-related papers as open access without any additional fees. OSTP has apparently decided that these adjustments have prepared the industry to survive even greater access levels.”
One provision requires a digital identifier, like a DOI, for all data and documentation. The policy memorandum argues the benefits of open access became apparent during the pandemic, when it accelerated researchers’ understanding of the virus and the development of a vaccine. Acting head of the OSTP Alondra Nelson expects the change will lead to gains across society. She stated:
“When research is widely available to other researchers and the public, it can save lives, provide policymakers with the tools to make critical decisions, and drive more equitable outcomes across every sector of society.”
Publishers have some time to pivot—the policy goes fully into effect in 2026. The article notes they could still make a buck from these papers by creating versions with added features like integrated graphics / videos or cross-references to other studies. Will that be enough to sooth ruffled feathers?
Cynthia Murrell, September 7, 2022
Australia: Harbinger for Tech Giants and Their Exposed Quite Weak Spot?
August 31, 2022
The US technology giants color many discussions. Facebook seems to want everyone to live and work in a computer graphics generated world. Google allegedly wants to improve search. Yada yada yada.
The weak spot for most of these outfits is the perception that online provides a haven for bad actors. Among bad actors, one of the least salubrious niches is CSAM, jargon for child sexual abuse material. For some bad actors, the last couple of decades have been the digital equivalent of a Burning Man devoted to the heavy metal life of shadows.
True or false?
It depends on whom one asks. If you ask me and my team, the big technology outfits as well as the feeder modules like shadow Internet Service Providers have not taken enough positive steps to address the CSAM issue.
“Australia Orders Tech Giants Apple, Microsoft, Snap and Meta to Step up Actions against Child Abuse Material” may be a harbinger of what’s coming from other countries in 2023. The article from the estimable Epoch Times reports:
Australian authorities have ordered global tech giants to report on the actions they have taken to stop the spread of child sexual exploitation materials on their platforms and will impose penalties on non-compliant companies.
What happens if New Zealand, the UK, Canada, the US, and other like minded companies follow in Australia’s footsteps?
CSAM is a problematic and troublesome issue. Why is Australia taking this action? The Wild West, “I apologize, senator” approach has worn thin.
CSAM is a weak spot, and big tech and its fellow travelers will have to do some fancy dancing in 2023 in my opinion. It’s time for the night club to close.
Stephen E Arnold, August 31, 2022
EU: Ahead of the US But Maybe Too Late Again
August 30, 2022
When making up for decades of inaction, just create more bureaucracy. That seems to be the approach behind the move revealed in Reuters‘ brief article, “EU Mulls New Unit with Antitrust Veterans to Enforce Tech Rules—Sources.” The European Commission seems to think it might be difficult to force tech giants to comply with the recently passed Digital Markets Act (DMA). Now where would they get that idea? The write-up tells us:
“The landmark rules, agreed in March, will go into force next year. They will bar the companies from setting their own products as preferences, forcing app developers to use their payment systems, and leveraging users’ data to push competing services. The new directorate at the Commission’s powerful antitrust arm may be headed by Alberto Bacchiega, director of information, communication and media, in charge of antitrust and merger cases involving the tech, media and consumer electronics industries, one of the people [familiar with the matter] said. Bacchiega could also be assisted by Thomas Kramler, head of the unit dealing with antitrust cases in e-commerce and data economy, and currently spearheading investigations into Apple and Amazon, the person said. Both officials are already liasing with those at the Commission’s Directorate-General for Communications Networks, Content and Technology which will jointly enforce the DMA, a third person said.”
Conveniently, both Bacchiega and Kramler were away on vacation and could not be reached for comment. A spokesperson stated the Commission is shuffling employees, assigning about 80 staff members to enforce the DMA. We wonder whether that is enough to counter Big Tech’s corporate resources, even with a pair of seasoned antitrust veterans at the helm.
Cynthia Murrell, August 29, 2022
Meta: What Does the Modern MySpace Do?
August 24, 2022
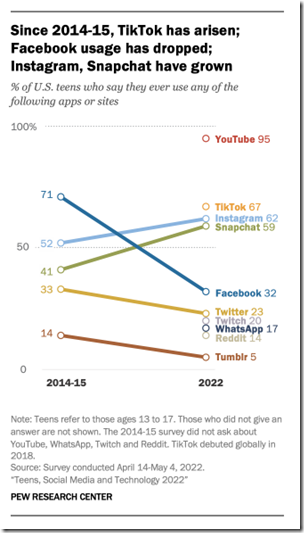
Frankly I don’t know what the Zuck and his team of wizards can do. I read “Teens, Social Media and Technology 2022.” The link leads to a study summary, a page of general info, and a summary of the Pew methodology.
One finding from the survey mavens at Pew Research caught my attention. If the methodology was on the money and the data processed in a way that kept the butcher’s thumb off the weighing pan, here’s a thrilling statement:
the share of teens who say they use Facebook, a dominant social media platform among teens in the Center’s 2014-15 survey, has plummeted from 71% then to 32% today.
In the span of 72 months, the Zuckbook watched teens who are considered a part of the future of the datasphere shift to short form videos. The write up included one of those charts colored in such a way to make legibility a bit of a joke. Here’s a screenshot with the bold blue line heading south. Note that despite the legibility, the other lines are heading up. YouTube is a floating dot at the top of the chart because, well, YouTube. Quasi-monopoly. Most popular online service in the “Stans.”
Should YouTube be worried? Not yet. The write up reports:
About three-quarters of teens visit YouTube at least daily, including 19% who report using the site or app almost constantly.
For more Pew data, follow the links in the cited article.
There’s not much analysis of the whys and wherefores, but the data are clear. The allegedly Chinese linked outfit TikTok has access to useful data from young people. What could a crafty person do with these data? Wait until one cluster identified as susceptible individuals and then approach or attempt to influence them.
Stephen E Arnold, August 24, 2022